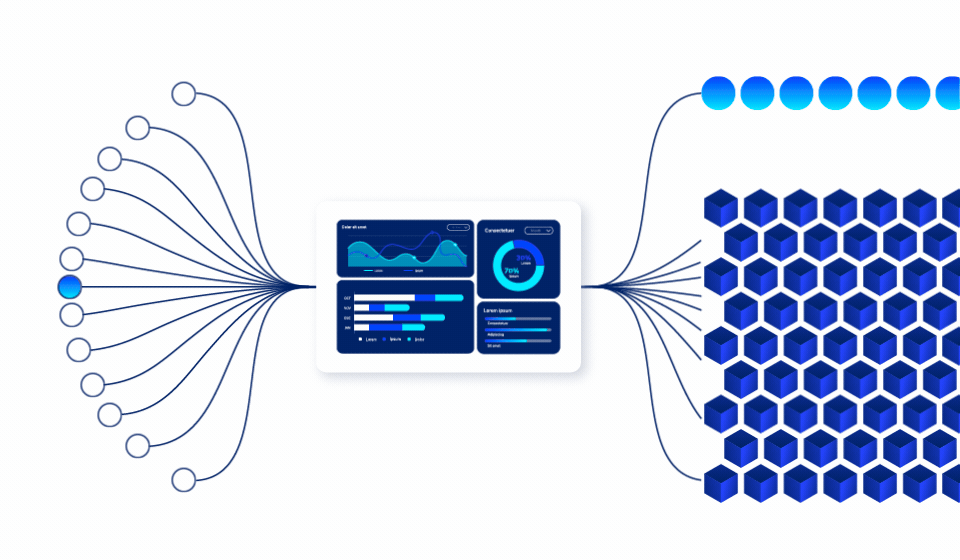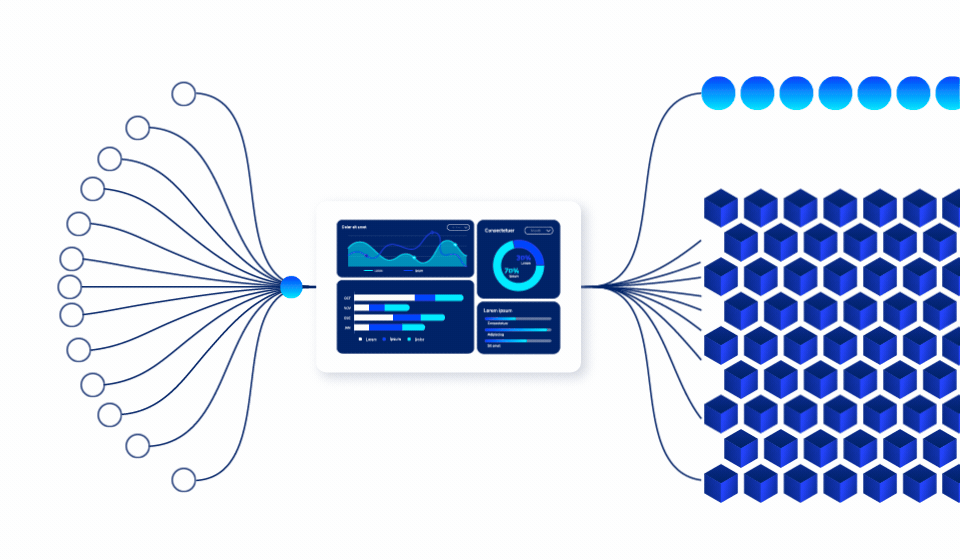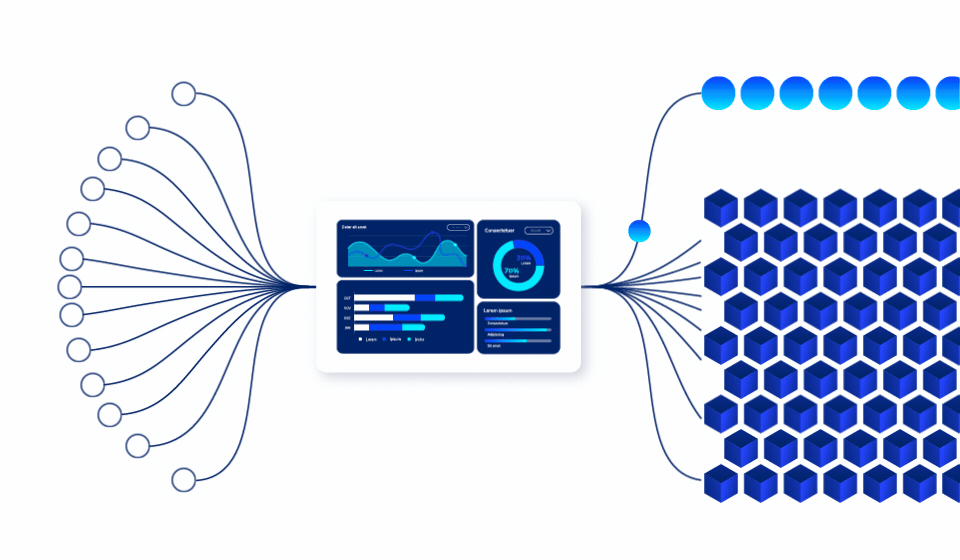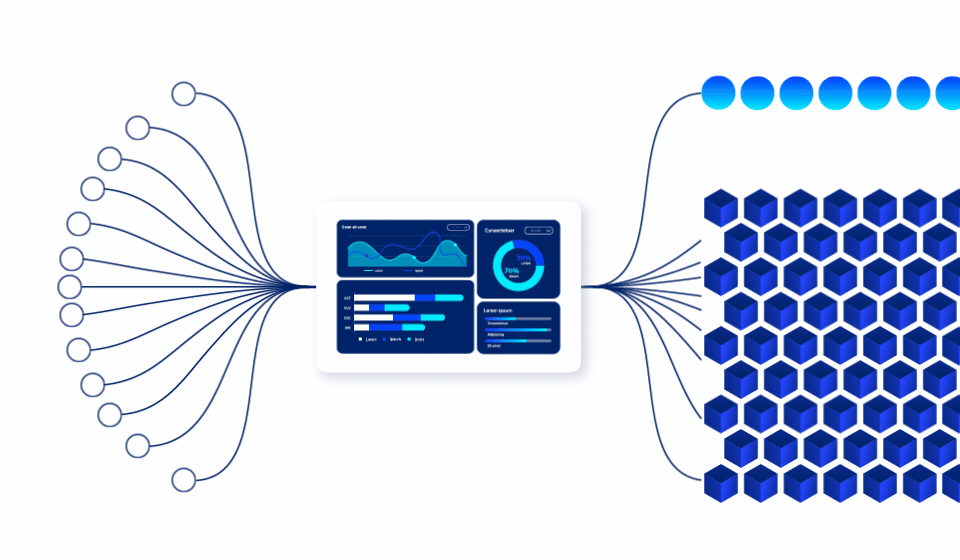
Next-Gen Data Loss Prevention (DLP)
Go beyond traditional DLP. Predict Which data will be used and stop unauthorized usage before it happens.
Go beyond traditional DLP. Predict Which data will be used and stop unauthorized usage before it happens.
Traditional DLP solutions react after data is already at risk. Ray Security’s predictive data security platform enables to:
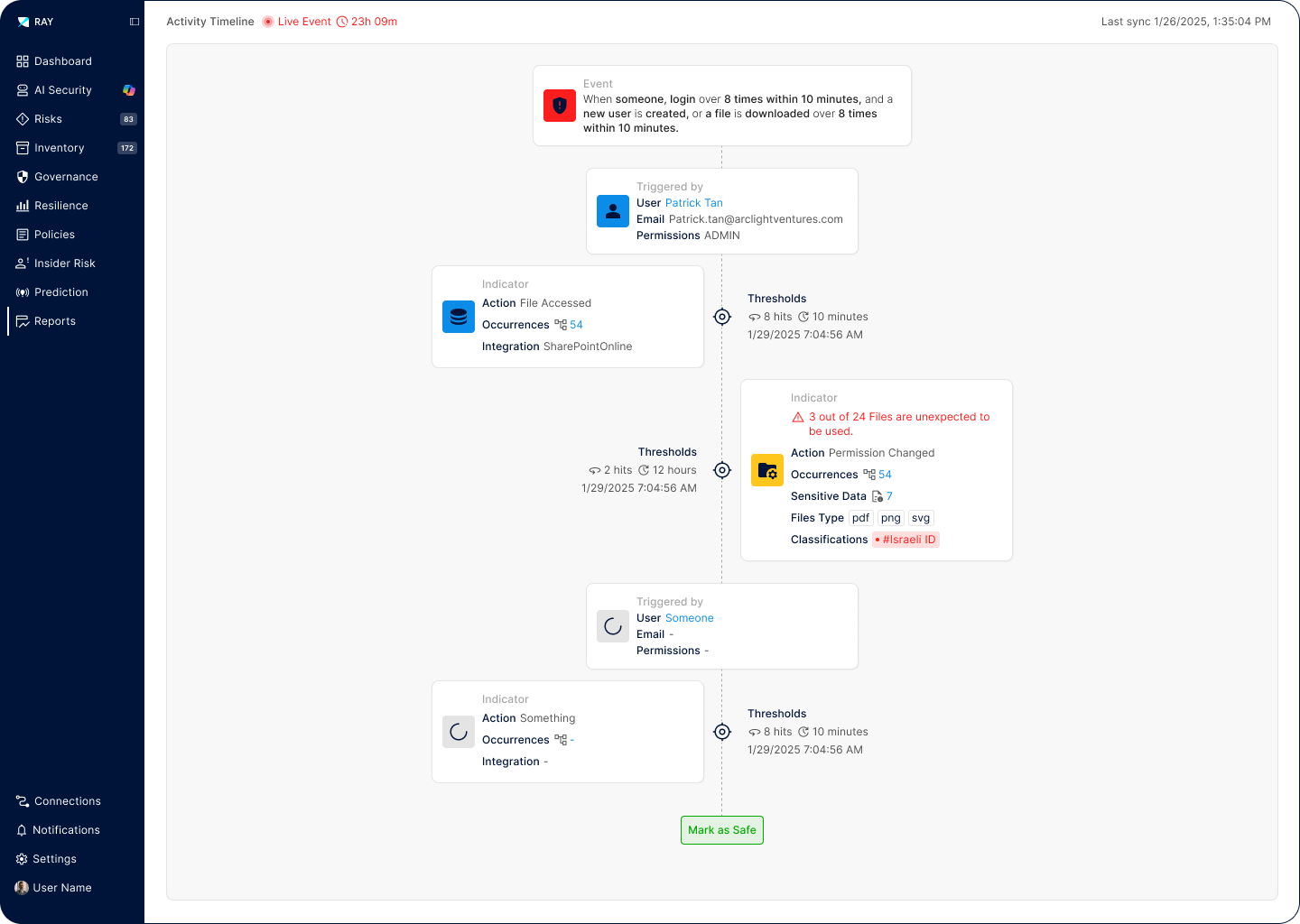
Our predictive engine identifies which data will be accessed, enabling proactive protection strategies that prevent unauthorized access before it occurs.
Track and monitor data as it moves across cloud, on-premises, and hybrid environments with comprehensive lineage and access justification for every interaction.
Automatically verify access justification, maintain privacy controls, and prevent unauthorized, uncontrolled, and unaudited data use across all environments.