Data Access Audit
& Investigation
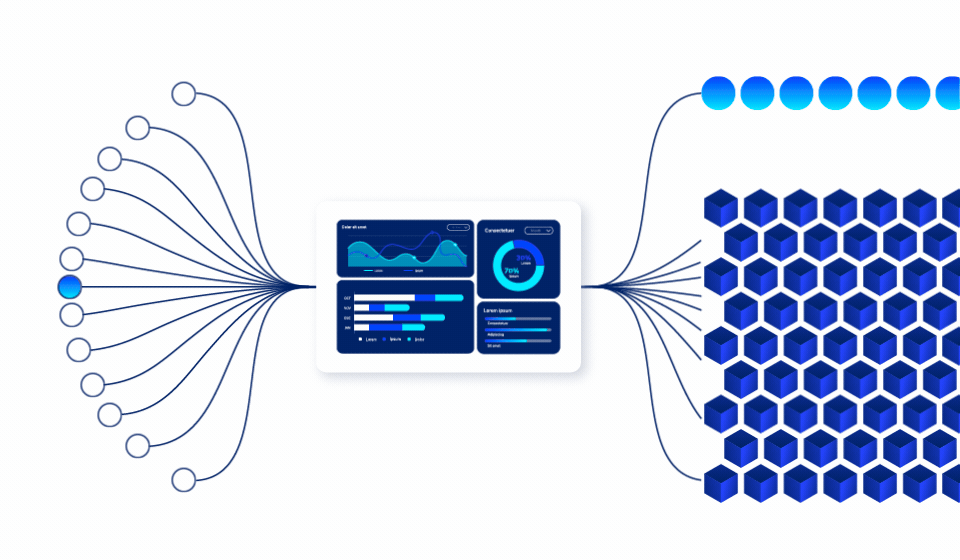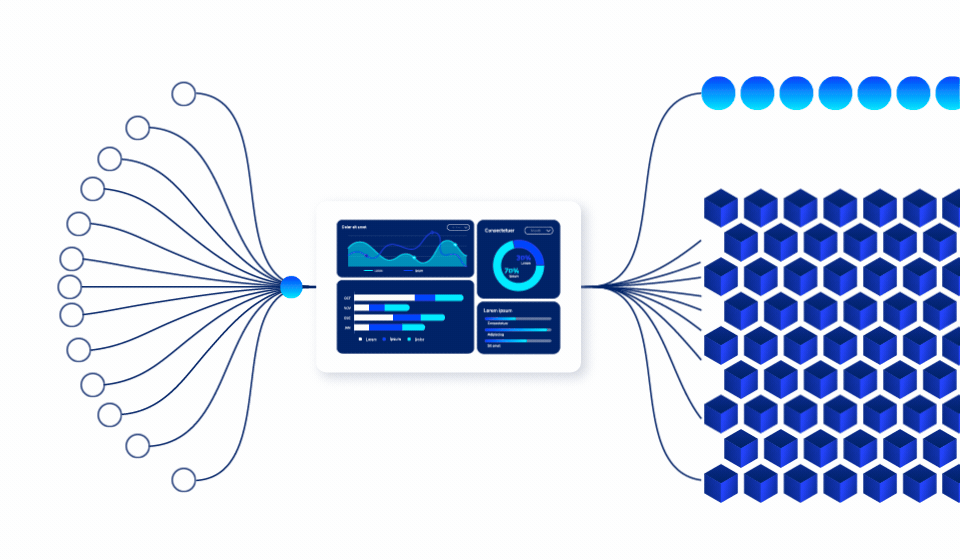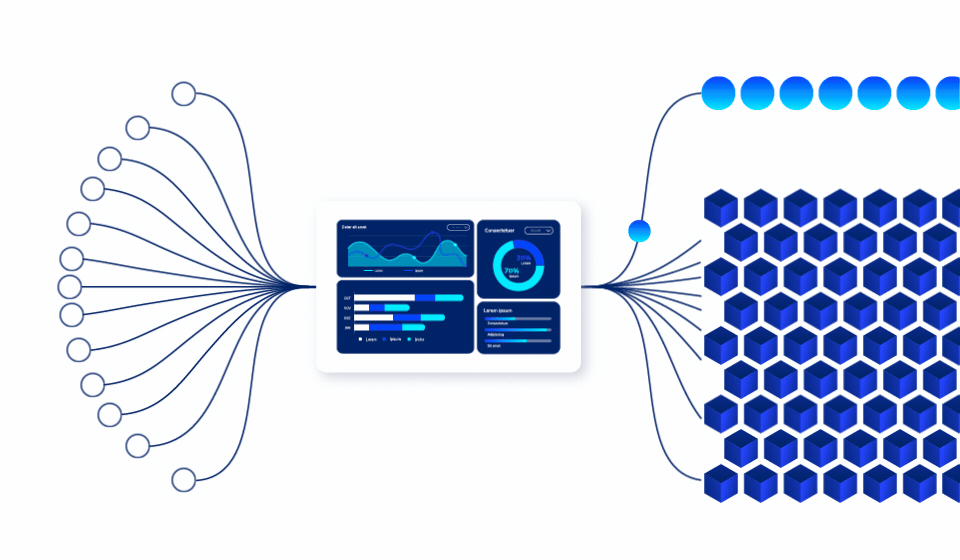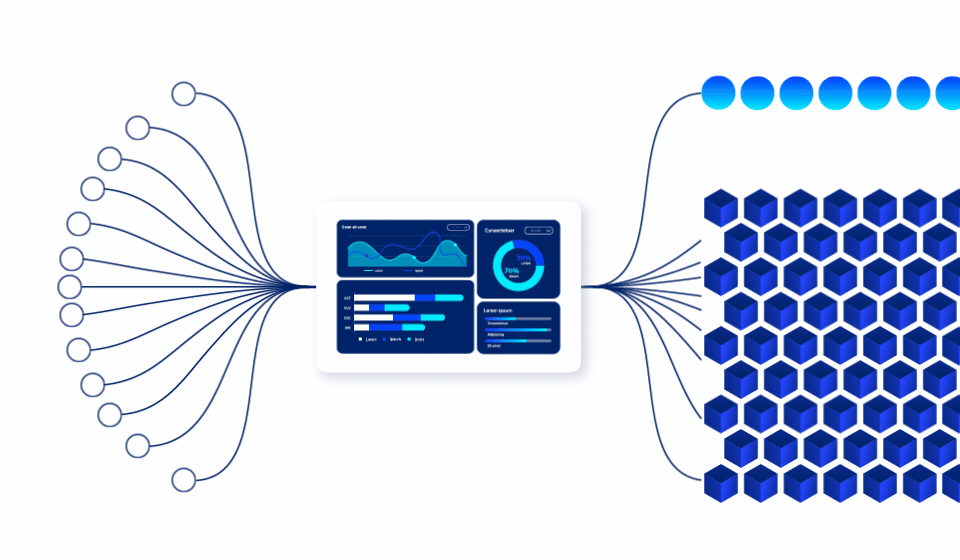
Complete visibility into who touched what and when
Complete visibility into who touched what and when
When a breach, audit, or anomaly occurs, organizations must answer a simple question: who accessed sensitive data? Most cannot do so with confidence.
Ray Security provides full visibility into data access activity, enabling teams to:
Identify every file accessed during a breach window, track the full scope of compromise, and provide board-level reporting with complete confidence.
Generate comprehensive access audit trails required by SEC, HIPAA, GDPR, SOX, and other regulations, without manual log aggregation.
Detect unusual patterns like bulk downloads, after-hours access, or suspicious file interactions that indicate potential insider threats or compromised accounts.