Why Everyone Is Nostalgic for 2016, And What It Reveals About Modern Cybersecurity

Why Everyone Is Nostalgic for 2016, And What It Reveals About Modern Cybersecurity
Scroll through TikTok or Instagram today and you’ll quickly notice a familiar pattern: throwback photos from 2016, vintage filters, and references to “the good old days.” What makes this trend noteworthy isn’t the aesthetics. It’s the tone. This isn’t ironic nostalgia or playful retro styling. It’s reflective. Sometimes even reflective.
Celebrities have joined in. Millions of posts reference the same year. Cultural commentators are taking note. The reason is simple: this trend isn’t really about a calendar year. It’s about how life felt.
You’ll sometimes see the phrase “2026 is the new 2016” used as shorthand. But few people genuinely believe the world is reverting to that earlier state. What they are reacting to is something deeper, a longing for a time that felt less overwhelming, less optimized, and less mediated by opaque systems and algorithms.
For many millennials and older members of Gen Z, 2016 has become a symbolic inflection point. It was pre-pandemic, pre-AI ubiquity, and before digital platforms fully transformed into attention-maximization engines. What resonates is not the year itself, but the psychological space it represented: connections felt lighter, platforms felt more playful, and technology still felt broadly additive rather than extractive.
That emotional shift mirrors something many professionals quietly feel in another domain: cybersecurity.
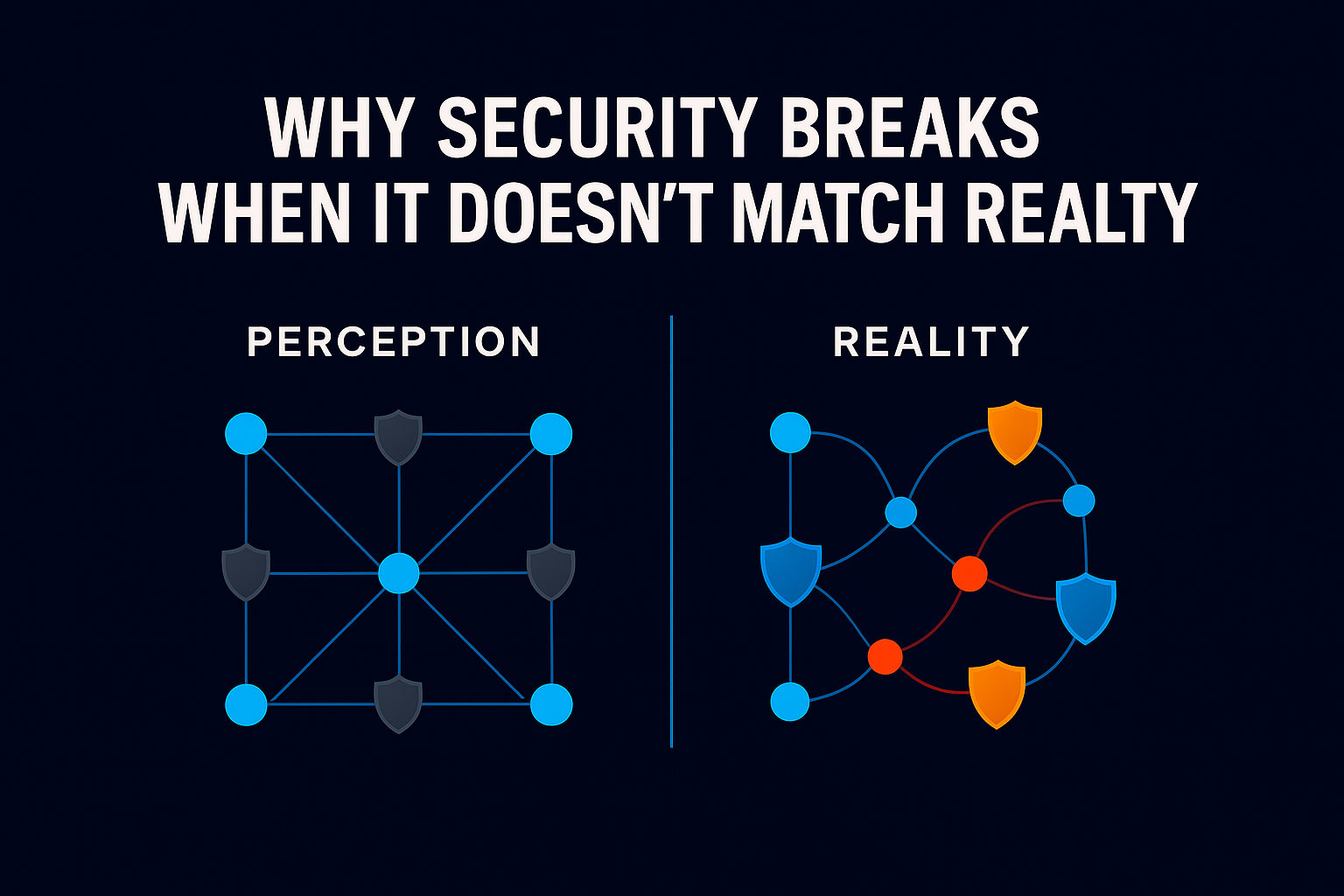
When Security Felt Easier to Understand
A decade ago, cybersecurity was already difficult, but it was easier to reason about. Threats were often visible. Attacks tended to originate externally. Security teams built mental models that separated “inside” from “outside,” trusted from untrusted.
When breaches occurred, they usually announced themselves. Ransomware encrypted files in plain sight. Malware generated unusual network traffic. Alerts fired, systems slowed, and response teams mobilized. Leaders might not have liked the outcome, but they generally understood what had happened and why.
That clarity mattered. It created confidence that risk, while serious, was at least observable and explainable.
Today, that clarity has largely disappeared.
Quiet Breaches And Legitimate Access
Modern breaches rarely look dramatic. They unfold quietly, often over long periods, and frequently without triggering traditional alarms. Increasingly, attackers rely on stolen credentials, excessive permissions, and long-standing access that was never revisited.
This shift is well documented. The Verizon Data Breach Investigations Report, along with analyses from Microsoft , consistently shows that credential misuse and identity-based techniques are involved in the majority of breaches. In other words, attackers no longer need to break in. They log in.
From a defensive standpoint, this is a fundamental change. When malicious activity uses valid credentials and approved access paths, the signals security teams once relied on lose much of their value. What used to stand out as suspicious now blends into normal business activity.
Users log in. Sessions renew. APIs are called. Data is accessed, all legitimately, at least on paper.
Complexity Changed The Risk Equation
This evolution cannot be separated from how enterprise environments themselves have changed. In 2016, data was more centralized. SaaS adoption was growing but manageable. Cloud usage was significant, but not yet dominant.
Today, data is distributed across dozens, sometimes hundreds, of cloud services, collaboration platforms, and third-party systems. Access expands continuously as employees change roles, projects evolve, and AI systems are introduced with broad default permissions. Yet access is rarely reduced with the same urgency with which it is granted.
The result is that cyber risk has become structural rather than event-driven.
For boards, this shift complicates oversight. Risk no longer appears as a discrete incident, but as an accumulation of access decisions made over time, many of them reasonable in isolation, but dangerous in aggregate. Legacy security models, built around perimeters and episodic reviews, were never designed for this reality.
Why The Past Feels Safer, Even Though It Wasn’t
It’s tempting to conclude that cybersecurity was simply “better” in 2016. That perception is understandable, and misleading.
Organizations were breached then too. Attackers exploited vulnerabilities and social engineering techniques that defenders struggled to contain. The difference is not that the risk was lower, but that it was more legible.
What has changed is the shape of risk. Today’s threats hide in plain sight, embedded in normal access patterns and legitimate workflows. Breaches are harder to detect, harder to explain, and often harder to attribute to a single failure.
This is precisely why cultural nostalgia resonates. Just as people remember 2016 as a time before systems became relentlessly optimized and harder to trust, cybersecurity leaders remember earlier defensive models as simpler because they were easier to understand.
Visibility has given way to diffusion. Events have given way to exposure.
From Nostalgia To Strategic Clarity
The lesson for leaders is not to romanticize the past. Nostalgia is not a strategy.
But it does contain a signal worth listening to. Systems that are easier to understand are easier to govern. In cybersecurity, restoring clarity, around who has access, why they have it, and whether it is still justified, has become one of the most pressing leadership challenges.
For CISOs and boards alike, the advantage going forward will belong to organizations that align security controls with how data is actually used, not how it was once assumed to be used.
In an era defined by complexity, clarity is no longer optional. It is a strategic necessity.
And unlike nostalgia, it’s something leaders can still design for.