Who Touched What, And Why Permissions Aren’t Enough

Who Touched What, And Why Permissions Aren’t Enough
When something goes wrong, whether it’s a suspected breach, a regulatory inquiry, or an internal anomaly, organizations face a deceptively simple question:
Who accessed the data?
Not who could have accessed it. But who actually did.
For many security teams, this is the moment when confidence begins to fade. Despite years of investment in access controls, reviews, and policies, the answers are often incomplete, slow to assemble, or based more on inference than on concrete facts. That gap is becoming increasingly difficult to justify.
Permissions Create Comfort, Not Evidence
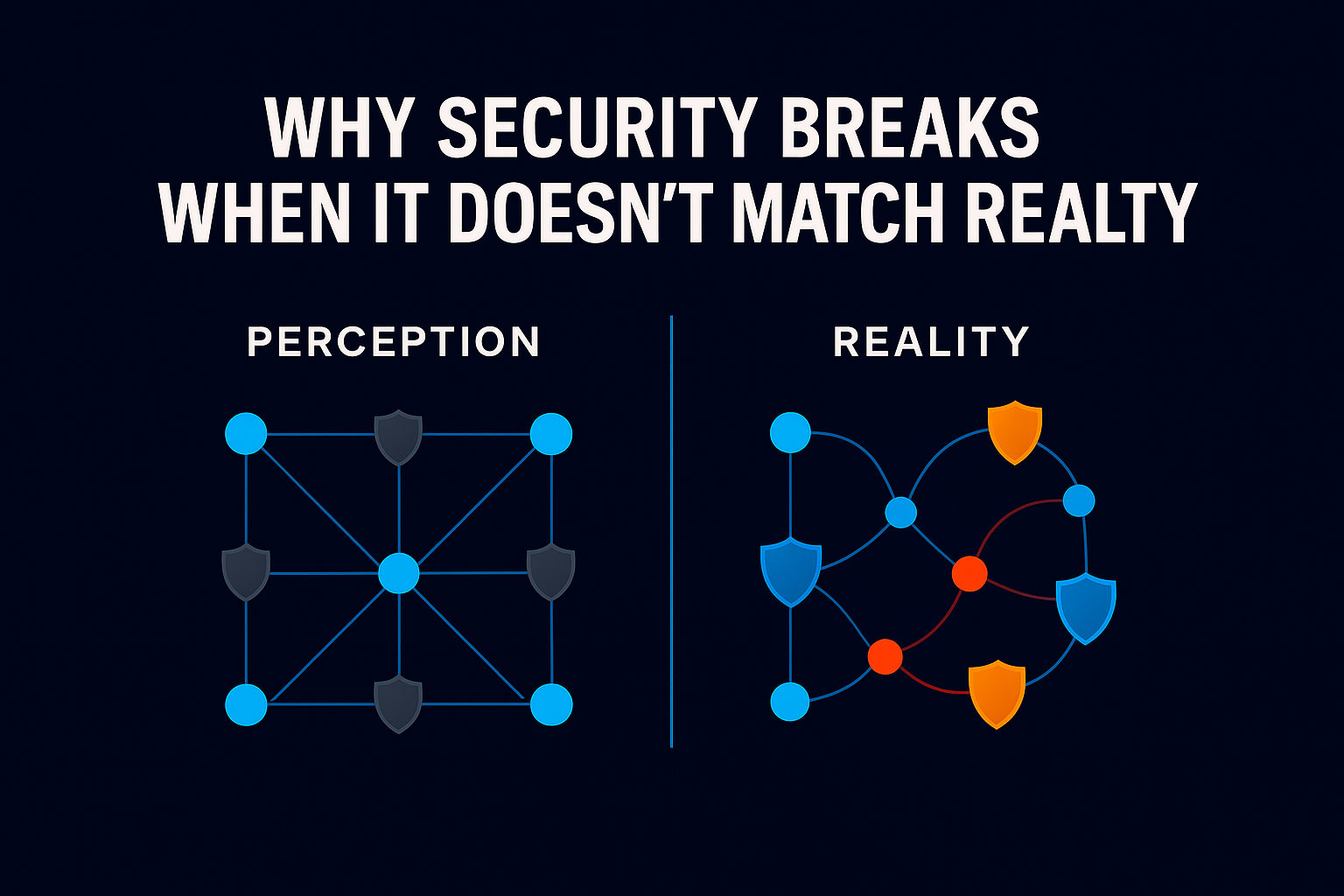
Most organizations believe they have a firm grip on data access because they understand permissions. They can show which users and groups are entitled to access specific systems, folders, or files. On paper, this suggests control.
In reality, it is only a partial view.
Permissions describe potential access. They do not describe behavior. A permission cannot tell you whether a file was opened, downloaded, accessed once or repeatedly, or whether that activity aligned with legitimate business needs.
Yet when incidents occur (or when auditors and regulators start asking questions) permissions are often all teams have to rely on.
That is not evidence. It is an assumption.
When Assumptions Are No Longer Acceptable
The question of “who touched what” rarely emerges in calm conditions. It surfaces under pressure, after a suspected incident, during an audit, or when leadership is trying to understand impact and exposure.
In regulated industries, this question increasingly ties directly to obligations under frameworks such as GDPR, HIPAA, and financial regulations, as well as disclosure expectations enforced by bodies like the U.S. Securities and Exchange Commission.
It also comes from customers. Large enterprises now routinely ask vendors to prove how data is accessed, monitored, and protected.
In these moments, vague answers are not enough. Screenshots of permission settings or collections of raw logs do not provide clarity.
What is expected is proof.
Logs Exist. Evidence Often Doesn’t.
Most environments already generate access logs. The problem is not the absence of data, but the inability to use it effectively.
Access information is often fragmented across platforms, retained for limited periods, and difficult to correlate across identities, files, and timeframes. Turning raw activity into a coherent narrative requires manual effort and interpretation, often under intense scrutiny.
As a result, investigations drag on, reporting becomes defensive, and confidence erodes precisely when it is needed most.
What security teams actually need is not more logging, but a defensible view of real data access, one that can answer questions clearly, quickly, and without guesswork.
Why Point-in-Time Access Evidence Matters
Point-in-time access visibility changes the conversation.
Instead of debating what might have happened, teams can look back at a defined period and see exactly which sensitive files were accessed, by whom, and what actions were taken. That clarity shortens investigations, improves incident impact assessments, and makes regulatory and customer reporting far less painful.
More importantly, it replaces assumption with fact.
For organizations under regulatory scrutiny, this level of evidence is no longer optional. It is increasingly the difference between confident reporting and uncomfortable explanations.
This Isn’t Only About Breaches
While “who touched what” often becomes urgent after something goes wrong, its value extends beyond incident response.
Access evidence helps organizations validate that real-world usage aligns with business intent. It allows teams to detect risky patterns early, before they escalate. And it enables calm, confident responses to auditors and customers, without scrambling to reconstruct history.
In modern data environments, understanding actual behavior is just as important as defining access in advance.
A Necessary Shift in How We Think About Access
Access control will always matter. Knowing who can access data remains foundational.
But control without evidence is no longer enough.
Organizations that can confidently explain who accessed sensitive data, when, and how are better positioned to investigate incidents, meet regulatory expectations, and maintain trust, internally and externally.
Knowing who touched what does not replace access control.
It makes access control accountable to reality.
Where to Start
One practical way organizations close the evidence gap is by generating a point-in-time view of actual data access. Instead of reconstructing events after the fact, teams can see who touched what during a specific window and use that view to guide investigations, reporting, and follow-up decisions.
It is a small shift that often makes a disproportionate difference.
If you were asked today, could you answer who touched what, with confidence?