Why Everyone Is Nostalgic for 2016, And What It Reveals About Modern Cybersecurity
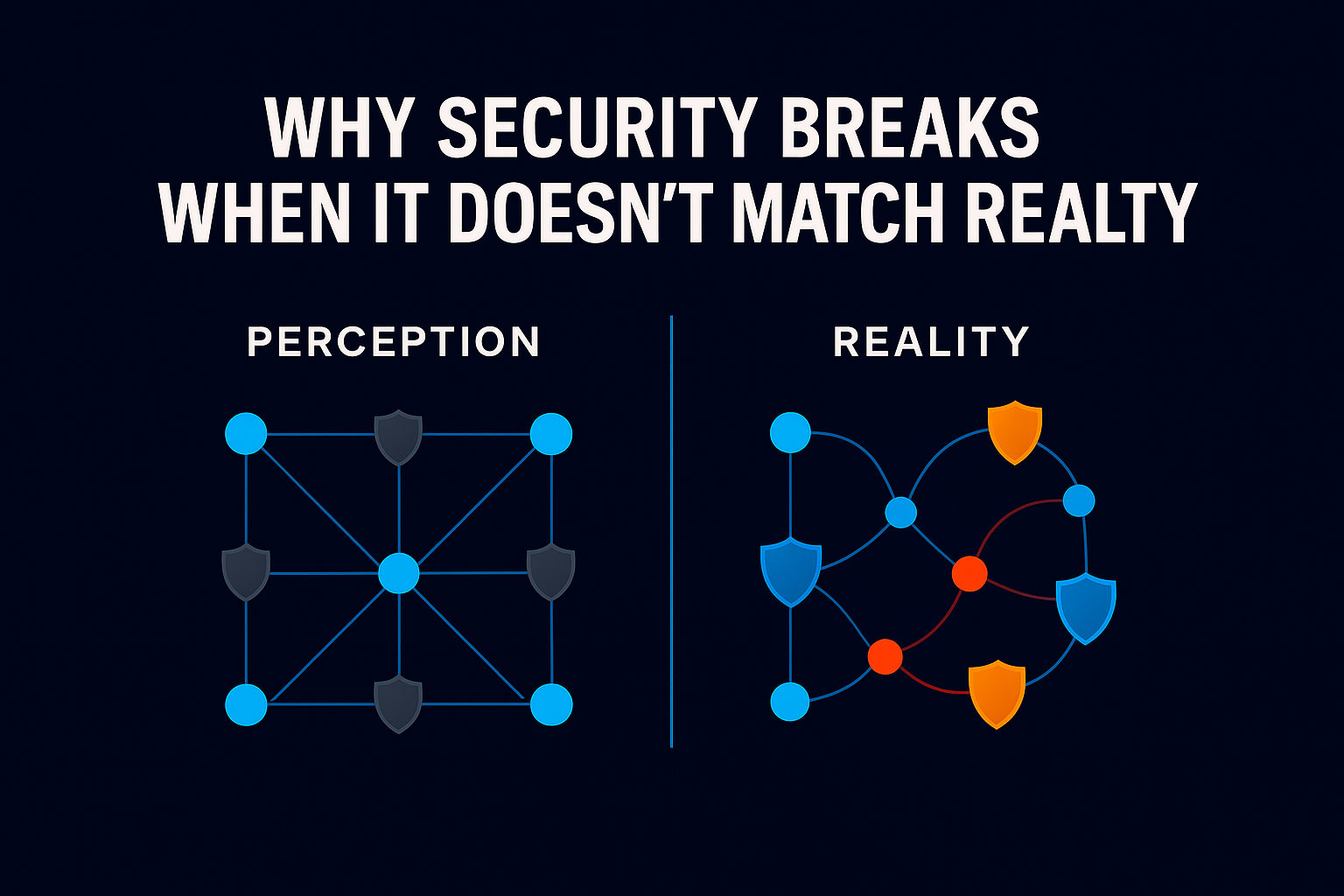
Why Everyone Is Nostalgic for 2016, And What It Reveals About Modern Cybersecurity Scroll through TikTok or Instagram today and you’ll quickly notice a familiar pattern: throwback photos from 2016, vintage filters, and references to “the good old days.” What makes this trend noteworthy isn’t the aesthetics. It’s the tone. This isn’t ironic nostalgia or […]