The Data Access Gap Putting Financial Institutions at Risk

The Data Access Gap Putting Financial Institutions at Risk
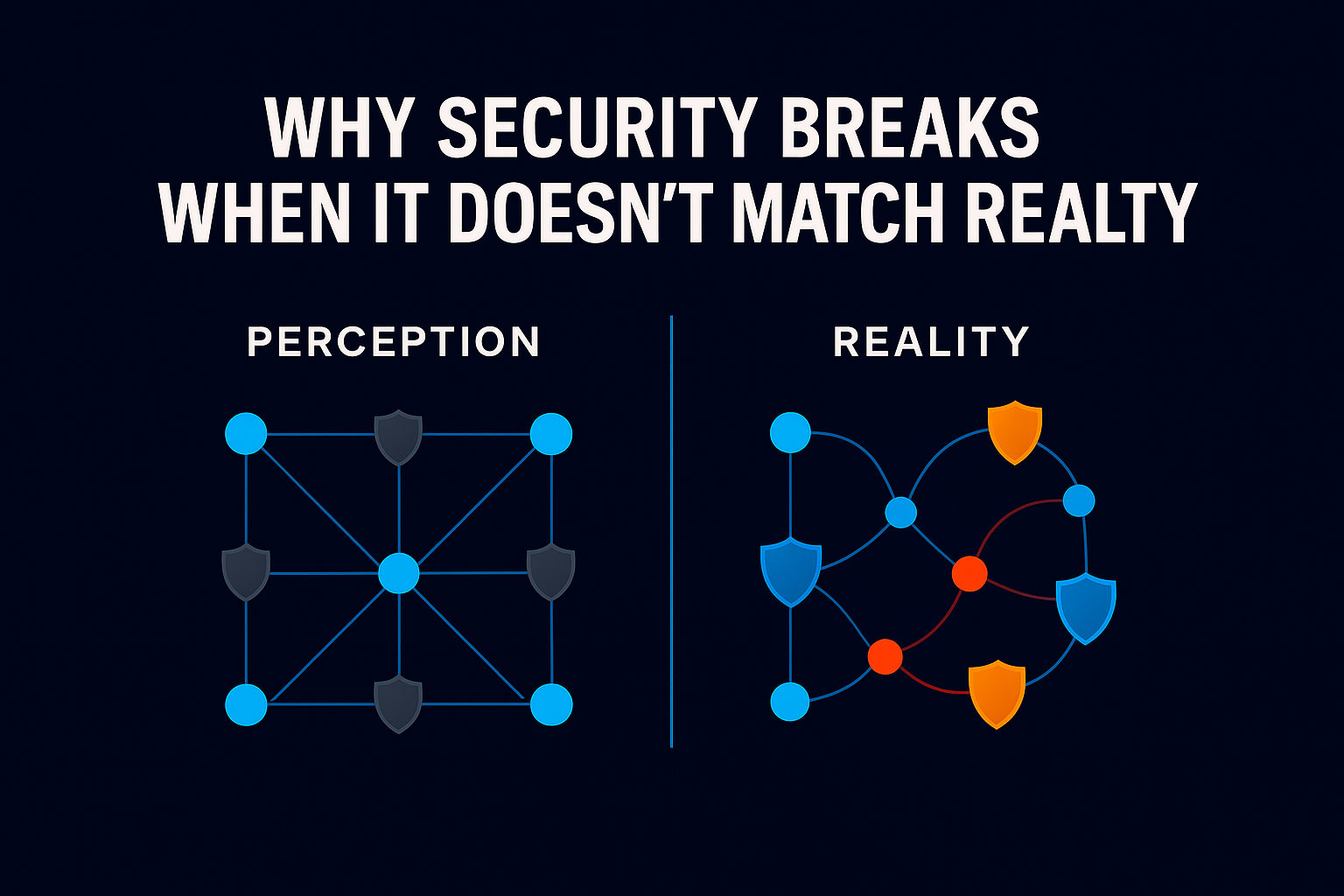
Data access almost always grows faster than it shrinks. This is even more true for financial institutions as it is a tangible risk on both the security and the compliance side.
New permissions are granted as people change roles, support projects, or onboard new systems. But those permissions are rarely revisited once the work is done. Over time, employees accumulate access they no longer use, and often no longer need.
This creates a widening gap between granted access and actual access use. And while this gap is rarely visible in traditional access governance programs, it has become one of the most persistent drivers of financial data risk.
From a security perspective, this is not a theoretical issue. It is a structural one.
Access Grows by Default, Not by Design
Most excessive access is not the result of bad intent or poor controls. It is the outcome of how access decisions are made inside large financial organizations.
Access is typically granted when someone joins a team, takes on a temporary project, or when systems are migrated or merged. It is granted when roles evolve faster than entitlement models can keep up.
What rarely happens is systematic access removal.
Temporary access becomes permanent. Legacy permissions remain “just in case.” And no one wants to be responsible for breaking a critical business process by removing something that might still be needed.
The safest decision is almost always to leave access in place.
Why Financial Institutions Are Especially Exposed
This problem is amplified in financial services.
Banks, insurers, and investment firms operate in environments shaped by decades-old systems that are still business-critical, highly fragmented application landscapes across business lines, and regulatory pressure that discourages aggressive change without certainty.
In this context, access governance becomes conservative by necessity. Permissions granted years ago for systems that no longer exist, or are no longer used, remain active because validating their removal feels riskier than leaving them untouched.
The result is an access footprint that reflects history, not current operations.
Why Access Reviews Don’t Reduce Real Risk
Most access reviews are designed to answer the wrong question.
They ask: Does this person need this access?
But reviewers are rarely given evidence of actual usage. Instead, they rely on role descriptions, institutional memory, or worst-case assumptions. If access might be required, it is usually approved. Over time, unused access becomes normalized and repeatedly re-certified.
From a CISO’s point of view, this creates a false sense of control.
Unused access still expands the blast radius of credential compromise, increases insider risk exposure, raises the impact of accidental data access, and broadens regulatory scope during audits and incidents.
Yet none of this is visible if access governance operates without usage context.
Unused Access Is Not Harmless
One of the most common misconceptions in identity and access management is that unused access is low risk.
In reality, unused permissions are often the most dangerous. They are less monitored, more likely to be forgotten, and persist across role and organizational changes.
From an attacker’s perspective, unused access is ideal. It provides pathways into sensitive data without triggering suspicion, because no one expects it to be exercised.
From a defensive standpoint, it represents exposure with no business upside.
The Metric That Reveals the Problem
When security teams look at access in aggregate, a clear signal emerges.
A large gap between granted access and used access indicates that permission models are misaligned with real work patterns, governance validates assumptions rather than behavior, and the organization’s identity attack surface is larger than it appears.
This is why access governance often feels busy but ineffective. Reviews are completed. Controls exist. But risk does not meaningfully decline.
The missing link is usage.
From Hypothetical Need to Observable Reality
Reducing financial data risk does not require more access reviews or tighter policies alone. It requires grounding access decisions in how data is actually used.
When access governance is informed by real usage patterns, security teams can identify permissions that no longer serve a business purpose, reduce exposure without disrupting operations, and focus effort on meaningful risk reduction rather than box-checking.
This shift, from theoretical need to observable behavior, changes the economics of access control. It allows institutions to remove risk confidently, rather than cautiously accumulating it.
A Closing Thought for Security Leaders
Access will always evolve. That part is unavoidable.
What is avoidable is allowing yesterday’s access decisions to define today’s data risk. The institutions that make real progress are not the ones that review access more often, but the ones that understand how access is actually used and align controls accordingly.
When access governance reflects reality, risk becomes measurable, manageable, and ultimately reducible, but is your access model built around how data might be used, or how it actually is used today?