Reduced Data Exposure
Cut data risk exposure to the absolute minimum
with predictive protection
Cut data risk exposure to the absolute minimum
with predictive protection
Most enterprise data sits dormant while creating massive attack surfaces. Ray Security’s predictive engine enables to:
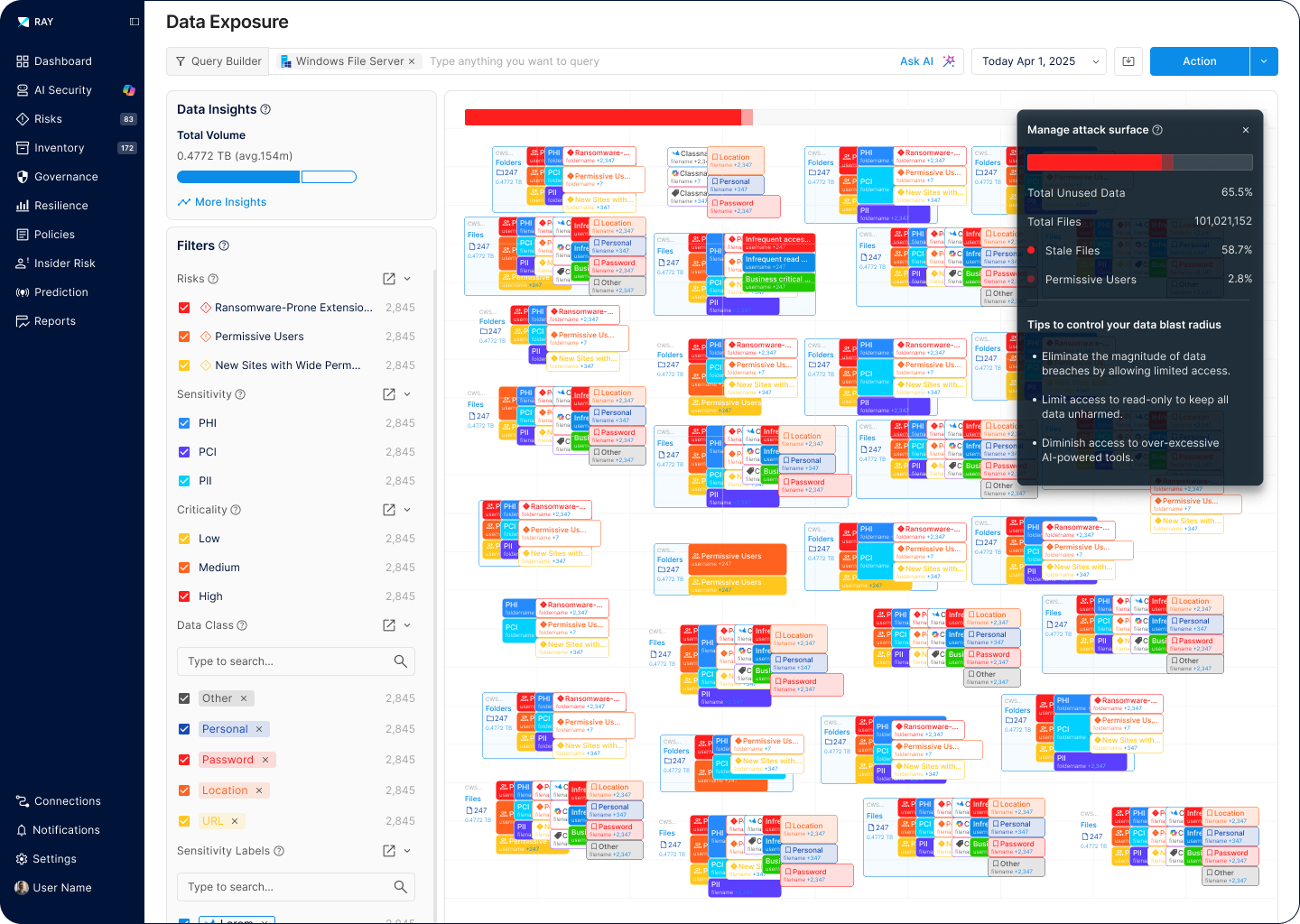
Reduce data exposure to the minimum by applying enhanced protection to data that will be used while making unused data immune to attacks.
Focus security resources on data that is actually used, enabling faster response times and broader protection coverage across your entire data estate.
Apply predictive protection to ALL data, including unclassified information, ensuring comprehensive security without manual classification overhead.