Ransomware Protection
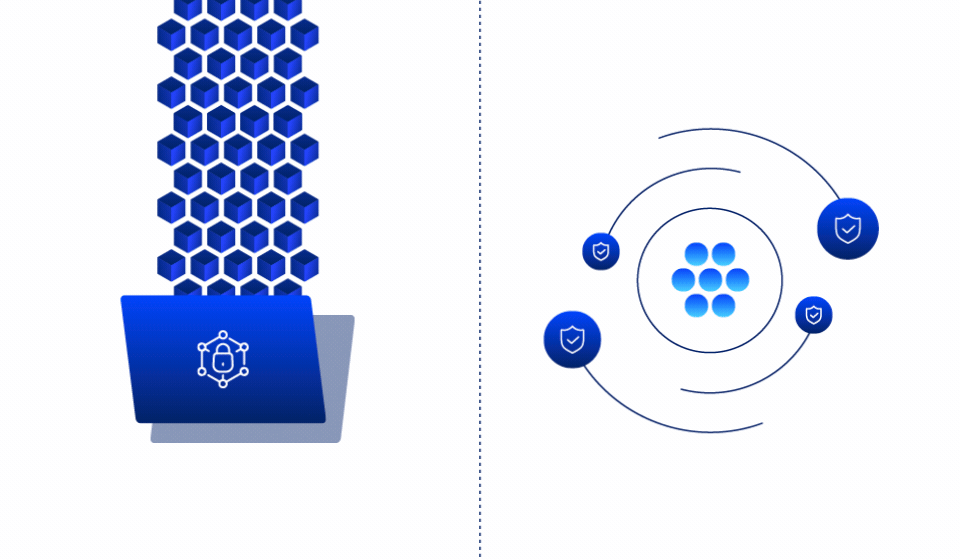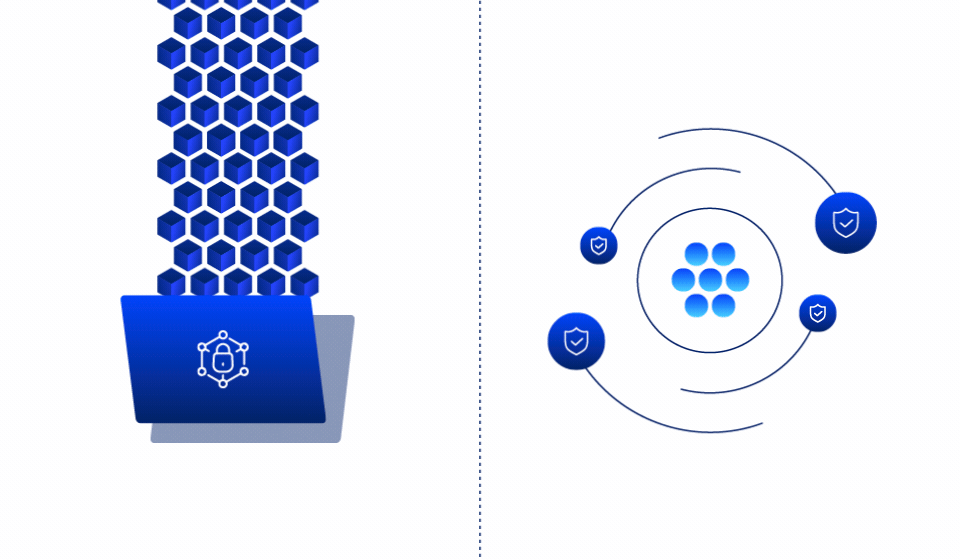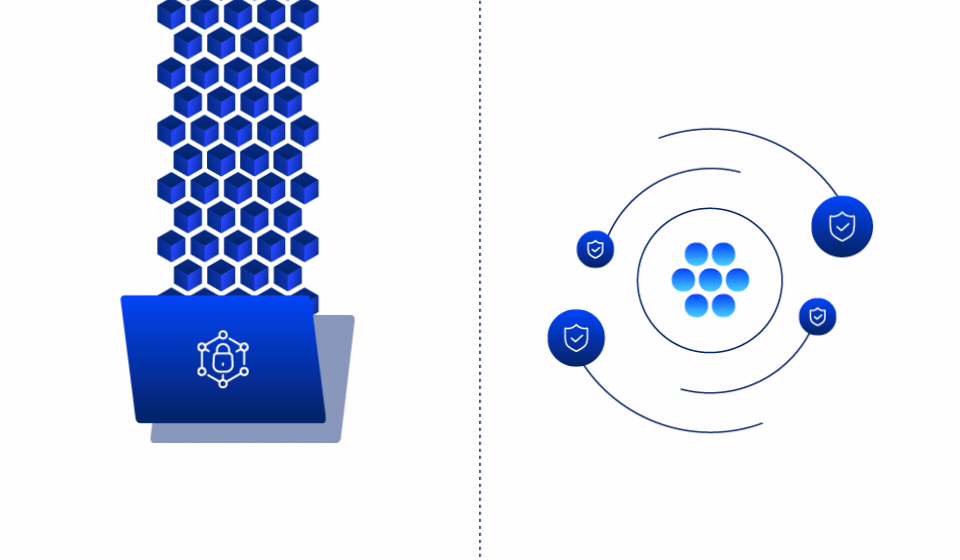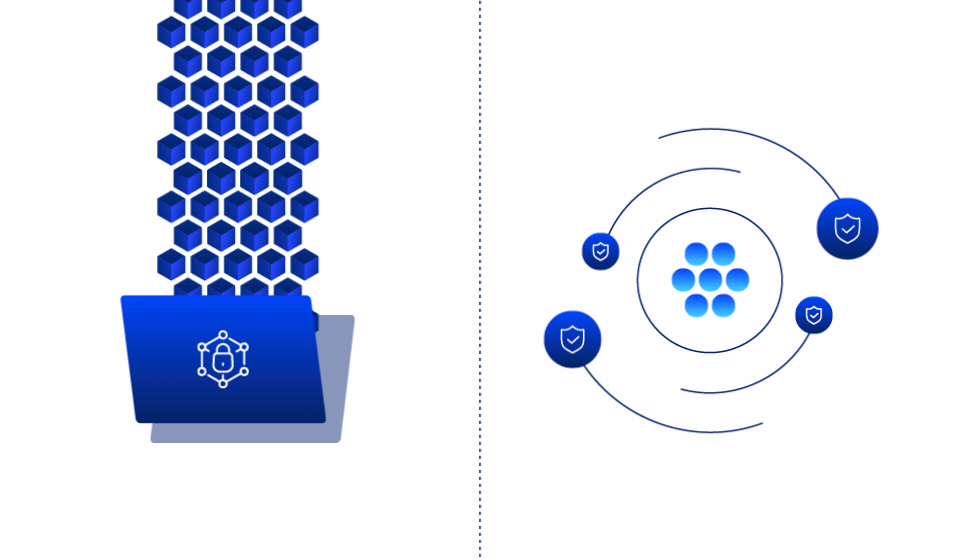
Make over 90% of your data immutable
by default
Make over 90% of your data immutable
by default
Traditional ransomware protection focuses on detection and recovery. Ray Security’s predictive approach enables to:
Automatically make unused data immutable based on predictive intelligence, preventing ransomware from encrypting the vast majority of your data estate.
Continuously monitor and protect data that needs to remain writable, ensuring immediate detection and recovery capabilities for business-critical information.
Real time detection of encryption patterns with automated containment to prevent ransomware spread across your environment.