Insider Threat Defense
Minimize insider risk through real time
access control
Minimize insider risk through real time
access control
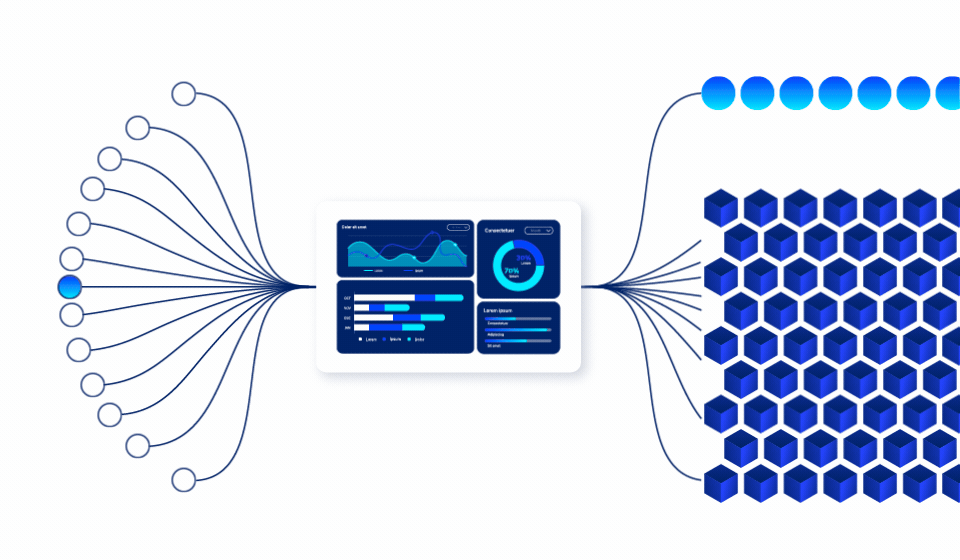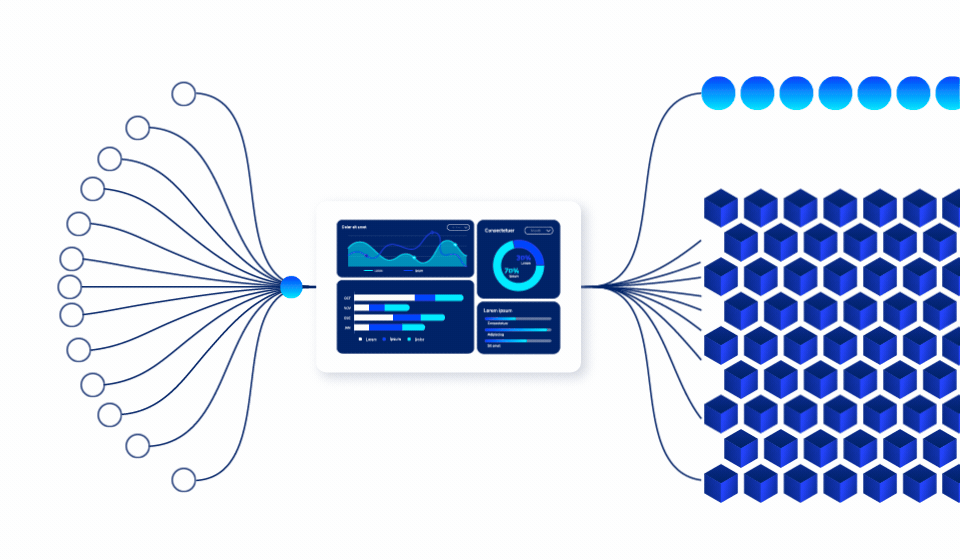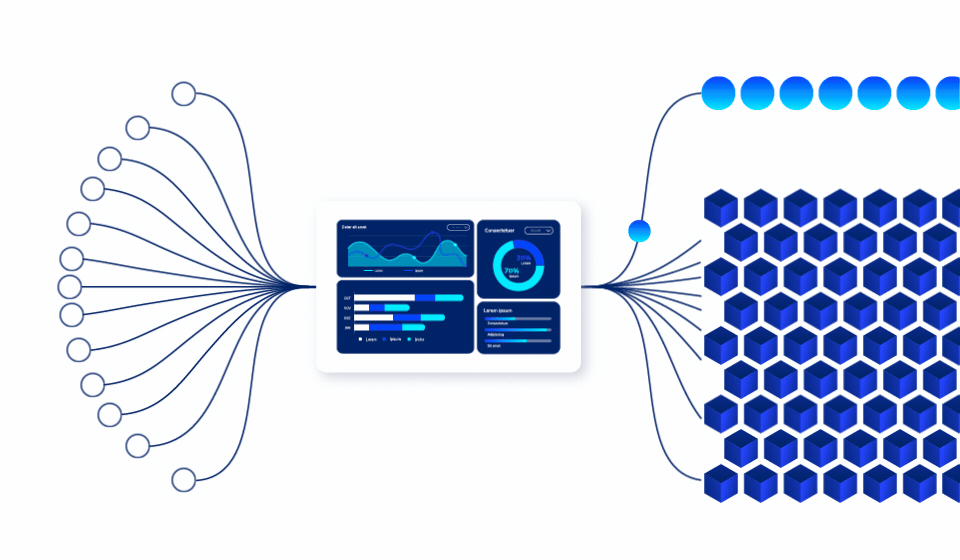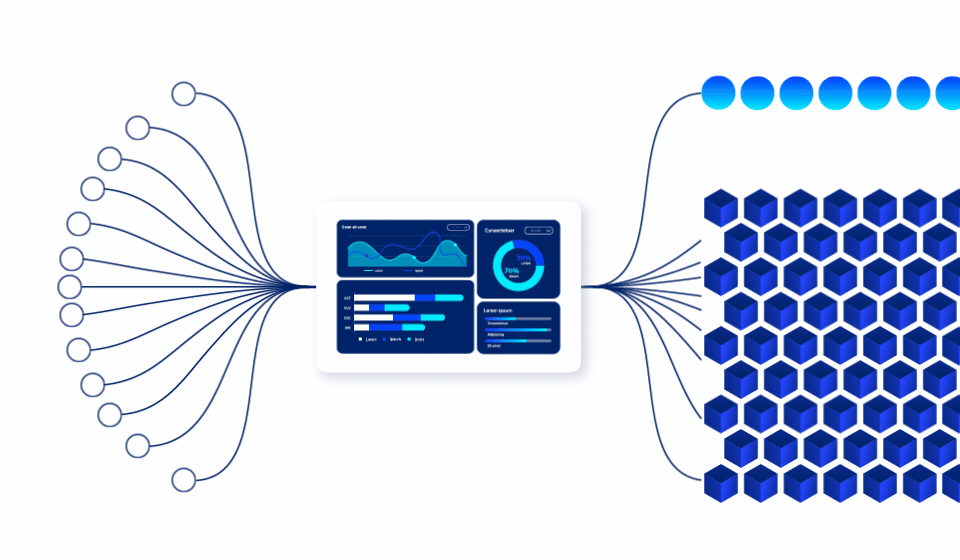
Insider threats are the hardest to detect because they come from authorized users. Ray Security’s predictive approach enables to:
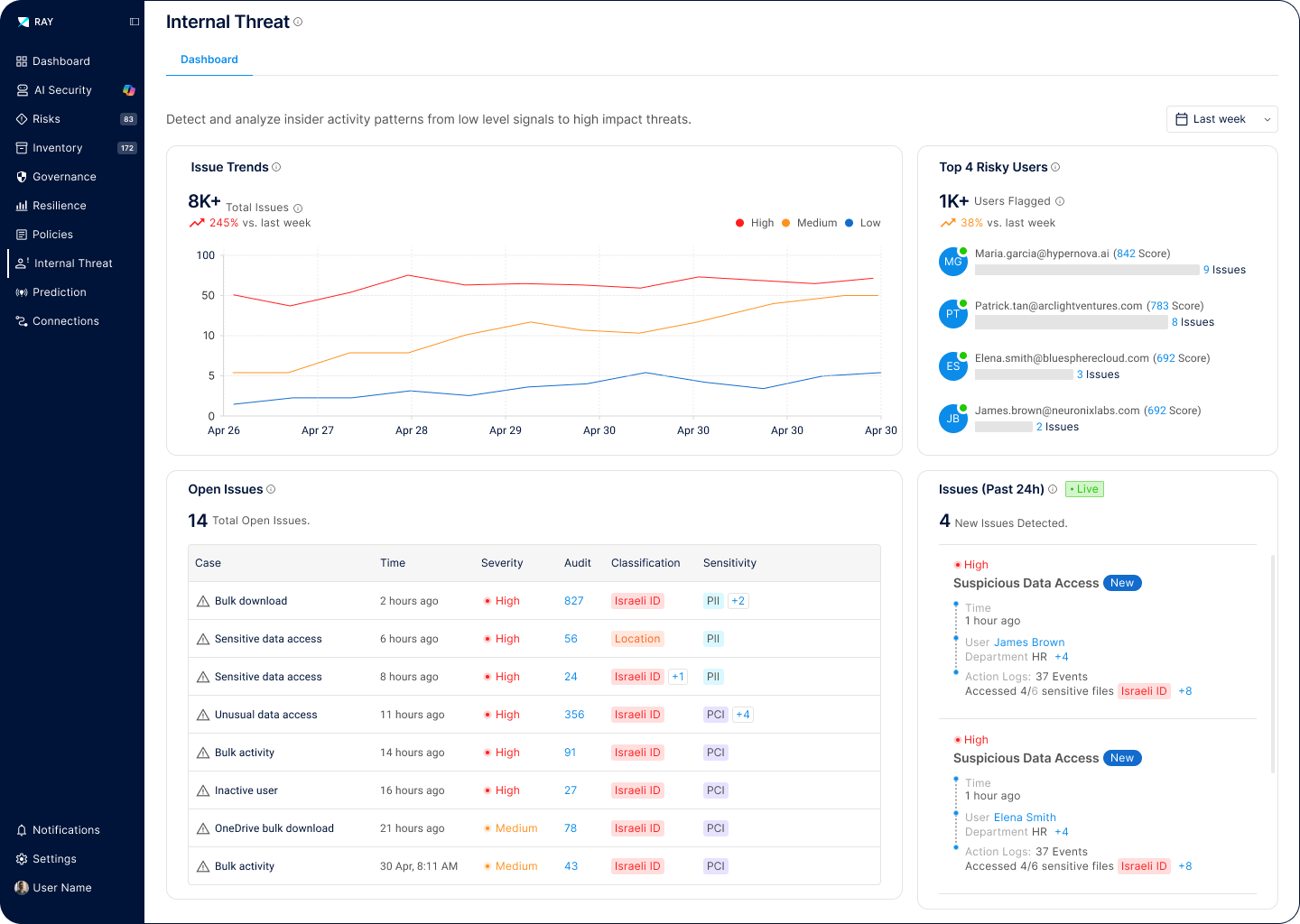
Our predictive engine identifies which data will be accessed, enabling proactive protection strategies that prevent unauthorized access before it occurs.
Automatically adjust data visibility based on business cycles, project timelines, and predicted usage patterns to minimize unnecessary exposure.
Implement granular, record-level access controls that dynamically adjust based on role, time, and business justification.