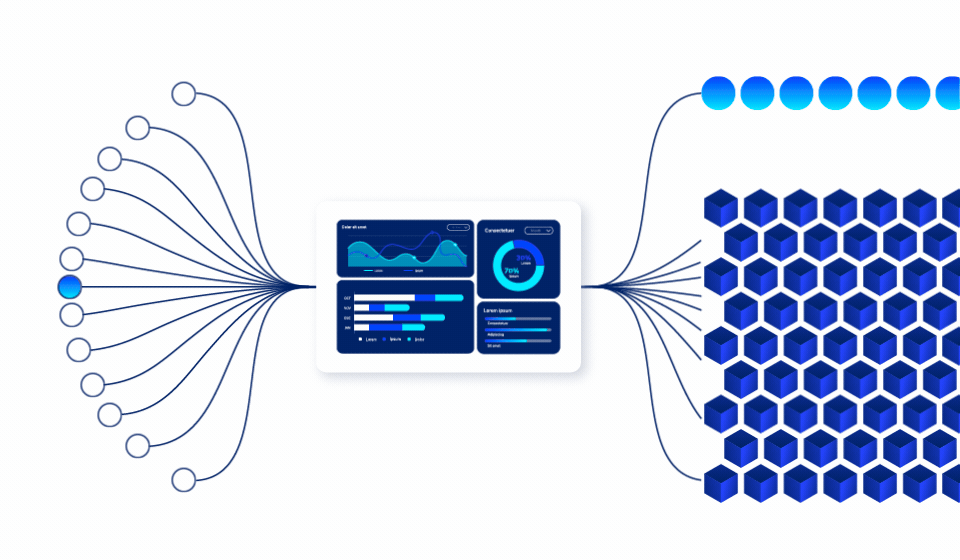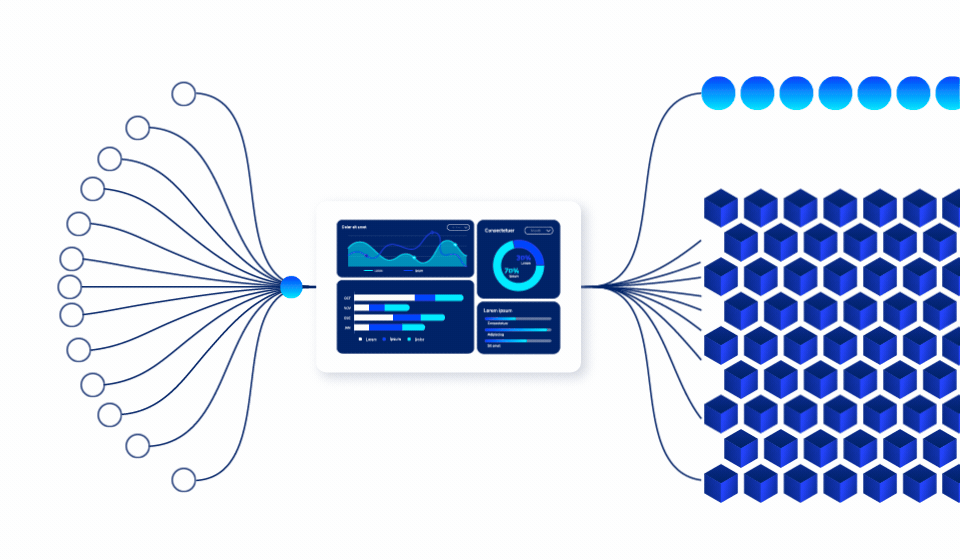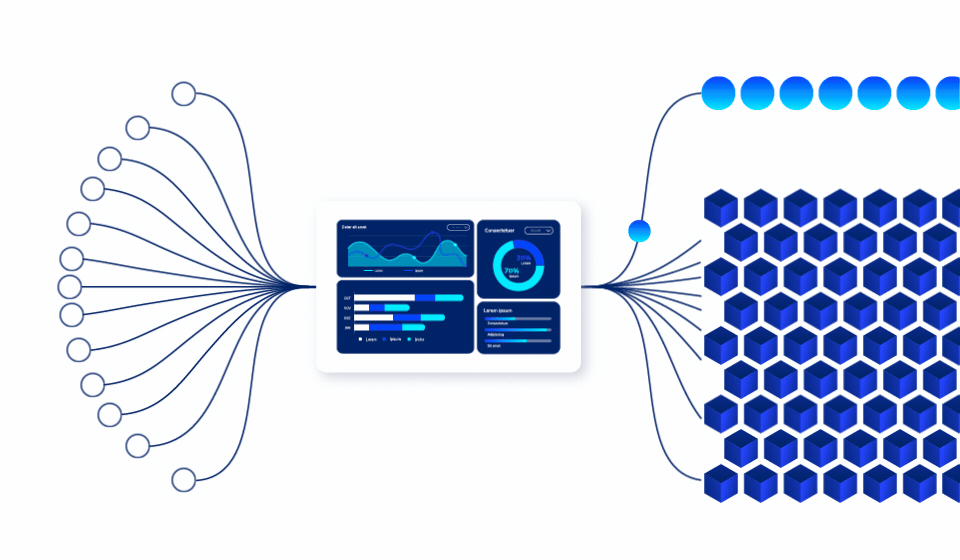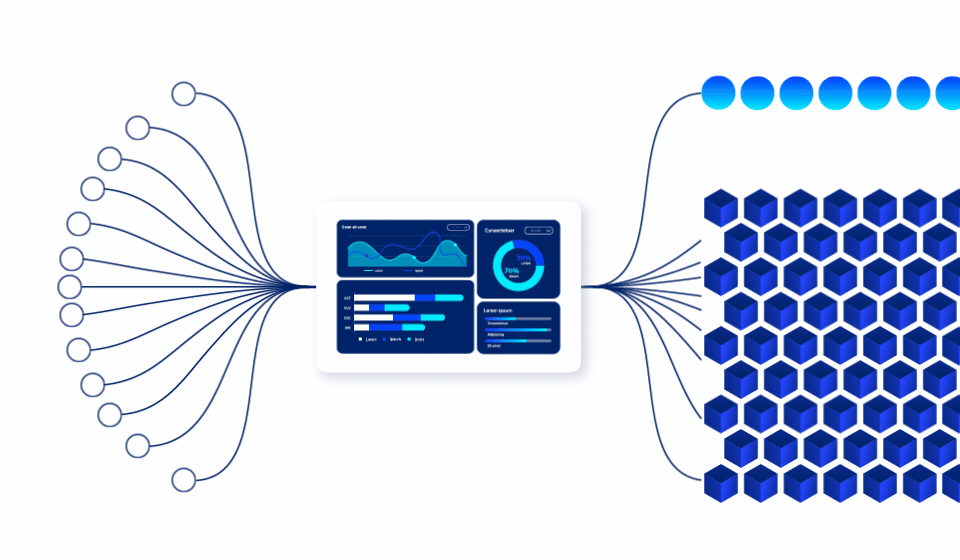
Data Access Review (DAR)
Enforce data access hygiene with Just Enough Access (JEA)
Enforce data access hygiene with Just Enough Access (JEA)
As organizations grow, permissions accumulate and drift away from actual usage, creating risk and compliance gaps.
Ray Security’s predictive data platform enables you to:
Map who can access data vs. who actually does, ensuring permissions align with JEA principles.
Identify and clean up unused or excessive rights before they become risks.
Automated reports prove compliance and reduce manual review work.