AI Data
Access Governance
Control what AI sees and secure it with confidence
Control what AI sees and secure it with confidence
AI tools like Copilot can access vast amounts of enterprise data, creating new risks for sensitive information exposure. Ray Security’s predictive data security platform enables to:
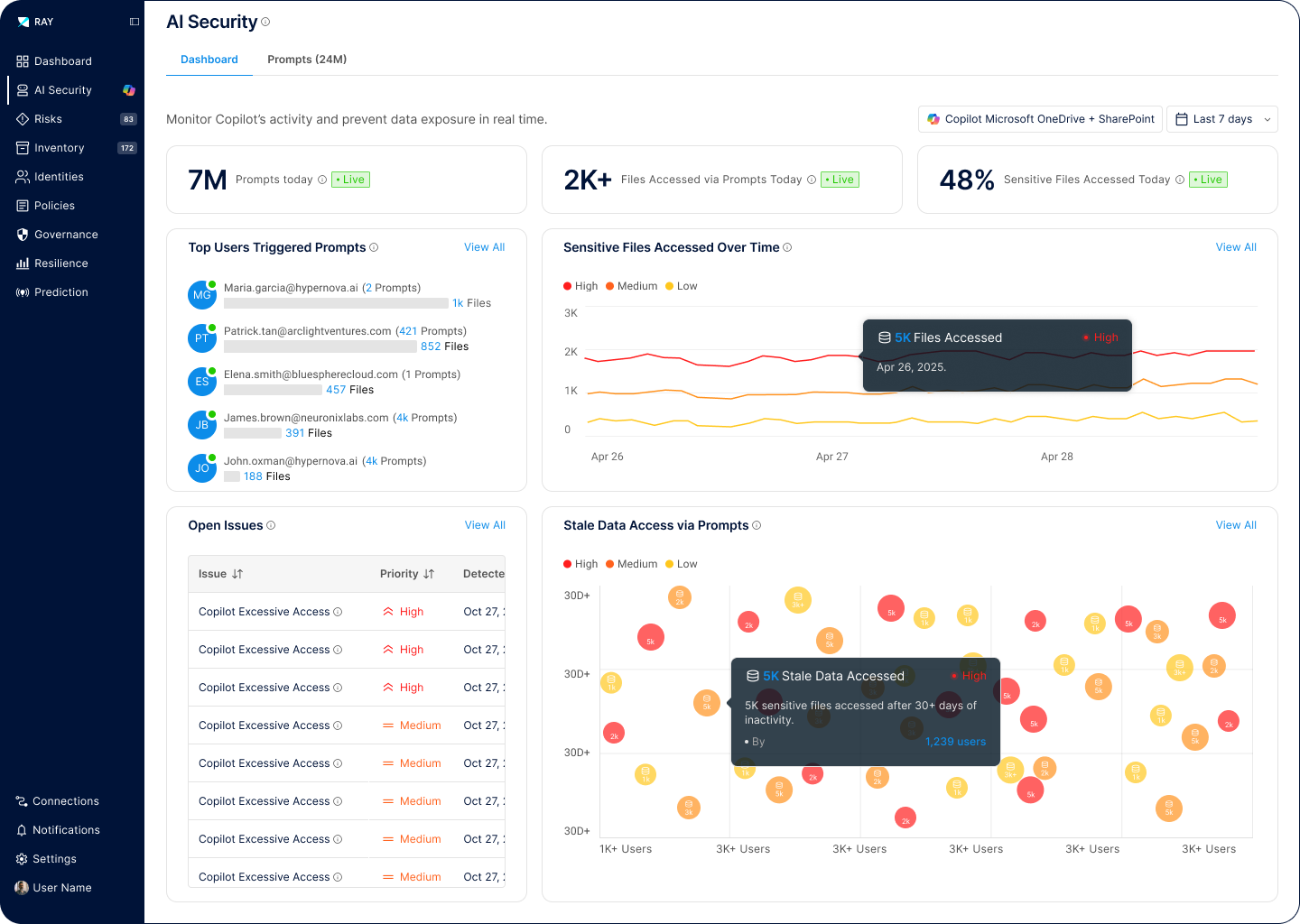
Precisely control which data AI tools can access based on sensitivity, user context, and business need, preventing unauthorized AI interactions.
Govern how agentic AI systems access and interact with enterprise data, ensuring autonomous operations remain within security boundaries.
Block sensitive content from being accessed or revealed in AI output.