Why Security Breaks When It Doesn’t Match Reality
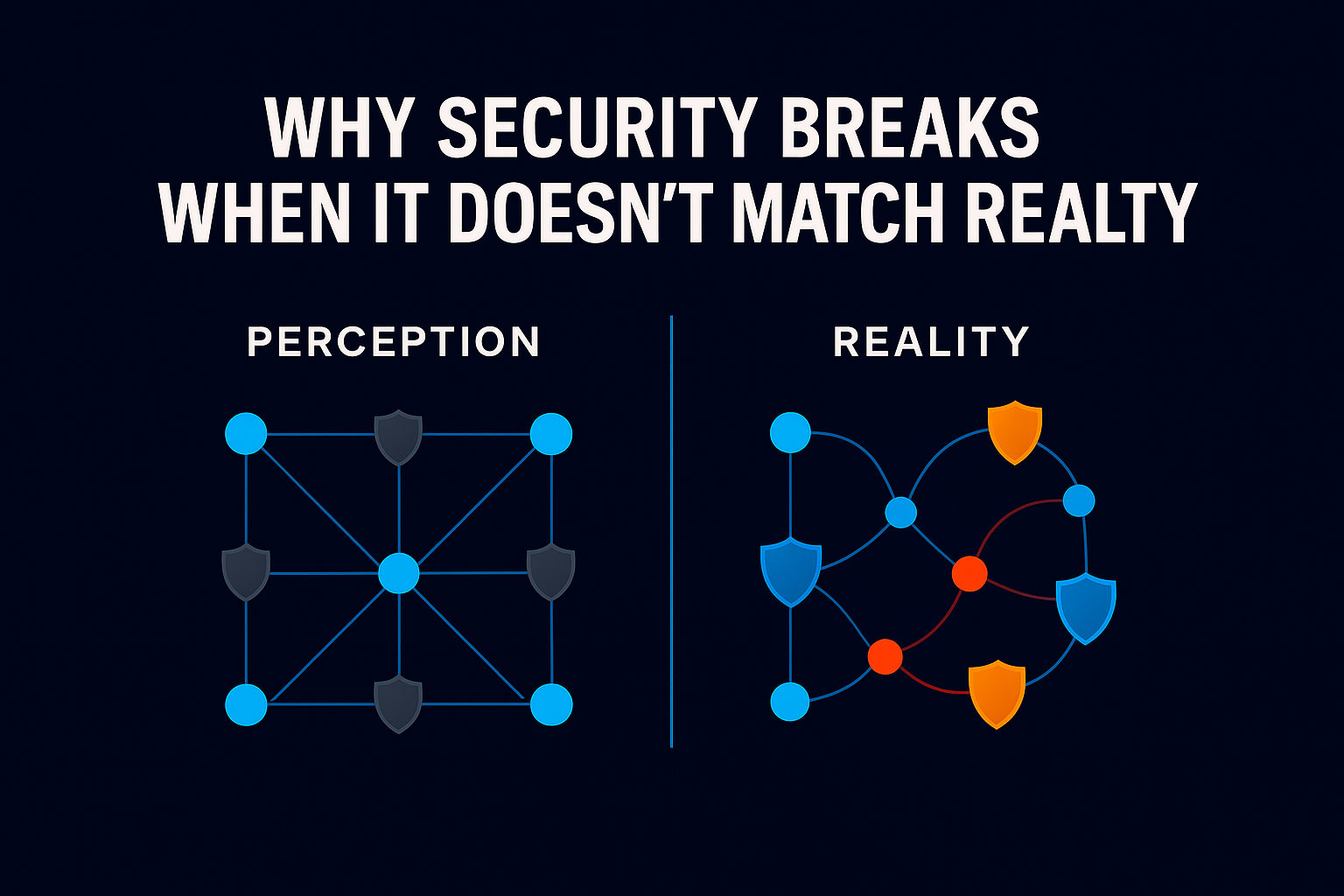
Security Is Out of Sync with How Data Is Used
Most data protection strategies still rely on static rules. They’re built around classifications, tags, or assumptions about what’s critical. But data doesn’t work that way anymore. It moves. It changes hands. It gains or loses relevance depending on time, task, and context.
Employees collaborate across departments, AI tools need access to multiple data sources, and business processes span cloud and on-premises environments. Static security policies can’t keep up with dynamic work patterns. The result is that security teams spend their time managing false alarms while real threats slip through gaps in protection.
The cybersecurity playbook that worked five years ago is failing today’s organizations. As threats evolve and business operations become increasingly digital, CISOs are discovering a fundamental problem: traditional data security doesn’t match how organizations actually use their data.
The Insider Threat Evolution: It’s Not What You Think
When most people think “insider threat,” they picture a disgruntled employee stealing data. That’s outdated thinking.
Today’s insider risks include:
- Compromised credentials that make external attackers look like legitimate users
- Well-meaning employees who accidentally expose data through poor practices
- AI systems and third-party tools with broad data access but limited oversight
- Contractors and consultants with temporary but extensive access needs
Traditional role-based access controls (RBAC) can’t address these scenarios because they focus on “who you are” rather than “what you’re actually doing with the data.”
CISOs need security that understands behavior patterns, not just permission structures.
The AI Wild West: New Risks, Old Tools
The rapid adoption of AI tools like Microsoft Copilot and ChatGPT Enterprise has created a data governance nightmare for security leaders.
The challenge: AI systems can access vast amounts of organizational data to provide insights and automation, but most organizations have limited visibility into:
- Which data these AI tools actually access
- How they use and potentially expose sensitive information
- What happens to organizational data once it’s processed by AI systems
The stakes: AI can inadvertently expose sensitive information through its outputs, creating compliance violations and competitive intelligence risks that traditional DLP tools weren’t designed to catch.
For CISOs, this means developing entirely new approaches to data access governance that can handle both human and artificial intelligence users.
Ransomware Reality: Beyond Backup and Hope
Traditional ransomware protection focuses on backup and recovery. That’s necessary but insufficient.
Modern approaches make most organizational data immutable by default while maintaining necessary flexibility for active business operations. They also:
- Detect encryption activities as they begin, not after damage is done
- Contain threats automatically before they spread throughout the organization
- Ensure recovery integrity with confidence in what data was affected
For CISOs, this means shifting from “how do we recover?” to “how do we prevent impact in the first place?”
Making the Business Case: ROI That Boards Understand
CISOs need to justify security investments with concrete business outcomes. Predictive data security delivers measurable results:
Risk Reduction: By focusing protection where it’s most needed, organizations dramatically reduce their attack surface. Less exposure means lower insurance premiums and reduced regulatory risk.
Operational Efficiency: Dynamic policies eliminate the manual overhead of static rule management, freeing security teams for higher-value work.
Business Enablement: When security adapts to business needs instead of imposing rigid barriers, it becomes a competitive advantage rather than a cost center.
Cost Optimization: Understanding actual data usage patterns helps identify waste and optimize storage costs while maintaining appropriate protection levels.
From Reactive to Predictive: The Security Evolution
The most forward-thinking CISOs are moving beyond the traditional “detect and respond” model toward predictive protection strategies.
Instead of asking: “What just happened?”
They’re asking: “What’s likely to happen, and how do we prepare?”
This shift involves:
- Understanding usage patterns to predict when and how data will be accessed
- Applying dynamic protection that strengthens automatically when risks increase
- Reducing exposure on data that isn’t actively needed for business operations
- Automating responses to emerging threats before they cause damage
The payoff is significant: organizations implementing predictive approaches report up to 90% reduction in data exposure risk while actually improving business efficiency.
The Solution: Security That Finally Matches Reality
The challenges outlined above, from insider threats to AI governance to ransomware protection, all arise from the same fundamental issue: security that doesn’t understand reflect how data is actually used..
CISOs need an approach that matches business reality. One that understands how information really flows, predicts where access will occur, and adjusts protections automatically based on context and risk. They need visibility that cuts through the noise so teams can focus on the threats that truly matter.
This is the vision behind Ray Security. Ray Security has developed the first predictive data security platform that solves this problem. Our platform analyzes how data is used, by people, systems, and AI tools, and predicts where risks are likely to emerge. Protection then adapts automatically, before threats can cause harm.
For security leaders who want protection that moves at the speed of their business, predictive data security isn’t just a shift: it’s the next standard.






